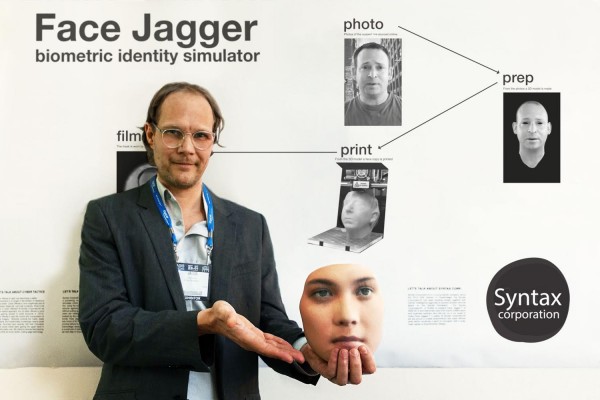
Face Jagger
Keywords: face jagger, jakob boeskov
Jakob S. Boeskov recounts his experience showcasing a fake cyber weapon at a security fair in Anaheim
Jakob S. Boeskov
Artist Jakob S. Boeskov recounts his experience showcasing a fake cyber weapon at a security fair in Anaheim, California. The fictitious weapon was presented at a rented booth to businessmen, terrorism experts, and federal employees.

Jakob S. Boeskov
Face Jagger, 2015
Flightcase, iPad, camera, 3D print
20 x 16 x 22 Inches
Preface
This was the idea: travel to America’s largest security fair and exhibit a fake cyberweapon. All the big boys in the surveillance industry would be there. Former CIA director Michael Hayden would be giving a keynote speech. In other words, this fair (ASIS 2015) would be the perfect place to present my brand new “pre-crime weapon”—a weapon that would help authorities “catch the criminal before the crime has been committed.”

I borrowed money from my PayPal card to get the project going. I created a fake website and called the organizers in Washington D.C. to present myself as a Danish cyber security entrepreneur based in Copenhagen and New York. I payed $5,200 to rent a booth under a fake name. The concept was that my weapon would allow federal agents to impersonate terrorists by using new 3D print technology. I called the weapon Face Jagger, a “de-criminalized” spelling of Face Jacker (as in ‘hi-jacker.’) I would create “spectacular simulations” which, when viewed online, would be perceived as reality.
This weapon would be brand new—from the future, even—but there would be nothing new about the concept. Camouflage and mimicry has been around since the age of the dinosaurs. The art of simulation is the art of survival. One might say that mimicry and simulation present something beyond good and evil. So on the surface, Face Jagger would be an antiterrorist weapon; an anti-ISIS weapon. However, on a deeper level, it would also be an anti-CIA weapon. The idea would be to investigate “military simulation.”
I had a stack of fake business cards made at a printshop in Chinatown and some 3D printed face masks made in Oregon and shipped to New York. Soon after this, I left for California, unsure of what to expect. On the plane, I worried about my visa situation. What would happen if I was found out? To ease my mind, I turned on the entertainment system.

Little Blue Boy Motel, Anaheim
I wake up in the cheap motel, stiff like a corpse. I can hardly move. Something is wrong with my back, my neck. I shower in the mold-infested bathroom, take some aspirin, put on my suit, and get ready to go. I am at the “Little Blue Boy Motel”—a place mainly frequented by Disneyland guests.
Outside, the sun is shining. Men in suits walk determinedly toward the convention center.

I slowly mix in with a group of ASIS attendees. A huge banner is hanging outside the Anaheim Convention Center. On it is an image of a soldier wearing what looks like a combination of virtual reality glasses and digital binoculars. Inside, a poster advertises a “Christians In Security Prayer Breakfast”. I have problems getting my credentials—perhaps because of my fake name. I start to sweat but I finally get them. Guards in black suits and Bluetooth headsets confirm my credentials at check points. Crowds are now milling in front of the escalators, which take us upstairs to The Grand Ballroom, where the official opening ceremony will take place. I find an empty seat and sit down. The stage curtain is blue and on it is projected, in white laser lights:
ADVANCING SECURITY WORLDWIDE
A uniformed marching band enters the stage. They play military march music. A group of young soldiers wearing khaki pants and green berets march into the hall from one of the side doors. Each soldier carries a flag and I think I spot the Iraqi flag and the Libyan flag and for a short moment I think that each flag represents a country that America has invaded in the last 10 years.
But each flag, of course, represents countries exhibiting at the fair. The soldiers now march toward the stage in military procession and, near the stage, they separate into two groups. The two groups continue marching toward the edges of the stage, where each flag is ceremoniously planted in a flag holder. Then, ASIS president Dave Tyson enters the stage at a brisk pace, almost running. All ASIS members and attendees stand up to clap and cheer. The ASIS president grabs a microphone, gives a brief talk, and introduces the main speaker: former CIA director Michael Hayden, who enters the stage from behind the blue curtain. He is a small, greasy man with rimless glasses. He looks over the crowd.
“Times are different now…”, he says, and begins a long talk about the Cold War, the internet, ISIS, WikiLeaks, the American-Israeli StuxNet cyber weapon, and the North Korean cyber attack on Sony. After the talk he says “Thank you” and disappears behind the blue curtain. Now, ASIS 2015 is officially open.

Jim & Lorene From State Department
The scope of the fair is vast—a stadium-sized space filled with large and small stands, all displaying new surveillance equipment, security software, and guns. The names of the corporations are futuristic and strange:
GAMMA 2 ROBOTICS
MAGNETIC AUTOCONTROL
ZODIAC AEROSPACE
NATIONAL CYBER SECURITY INSTITUTE
TIMEMASTER
I pass the enormous booth of G4S, a partially Danish-owned company and the worlds largest private prison operator. The corporation operates private prisons in USA and Israel and also operates what they call “interrogation chambers”—corporate speak for torture-chambers.
Back at my booth, I meet Brad from Los Angeles who looks at my poster.
“Is this what I think it is?” Brad asks, and he smiles.
“Yes,” I say, and give Brad a brief presentation and a business card.
“Impressive,” Brad says and leaves. I have been nervous about the possibility of being revealed as an imposter, but so far things seems ok. My next customers are Jim & Lorene from Washington D.C. They both work for the State Department. We exchange formalities and I explain the weapon to them.

“The main tenet—the main idea behind our product—is quite simple: cyber offense is now an American reality,” I say.
Lorene smiles and Jim moves closer to study the poster.
“ISIS is very clever at using social media,” I say with a stern and worried look on my face. “The threat is real. We are talking about thousands of young people who have left America to join ISIS in Syria.
“I see,” Lorene says and nods.
“Our technique is the following: From online photography we create 3D printed face masks. We then have so-called ‘body doubles’ wear the masks. The next step is to create videos with professional film directors, many of them based here in Hollywood…”
I point north to Hollywood and tell the couple about about Morten Storm, the Danish criminal who infiltrated Al-Qaeda. In a chapter in his autobiography he describes how his friend, a Somali Jihadi, beheaded a suspected spy.

“With our technology, we let ISIS do the dirty work. No American agent, soldier, or contractor will be in harm’s way. It’s a completely safe technology,” I say. Jim gives me his card and we agree to keep in contact.
Many more attendees come to the booth. After 5 presentations I go into the courtyard where I write down notes and get a Gatorade. I flip through the heavy ASIS catalog. With its cryptic, militarized computer phrases, it feels like a glimpse into the mind of a violent and paranoid computer programmer:
JIHADISM IN EUROPE
ADVANCED DARK WEB ATTACKS INTERPOL AND HOW IT HELPS YOU
HACKING THE INTERNET OF THINGS
Later, I am at the “President’s Party” in the courtyard in front of the exhibition area. A DJ (white, female) is playing political James Brown songs while I am handed free cigars by a military guy in a white cowboy hat. There are free drinks and free tacos and there is a yellow, dragon-shaped mascot with the words “SECURITY” printed on its stomach. I’m not really looking forward to the coming days. Tomorrow, there will be more of it: more nervous Iraq vets looking for jobs in the security sector; more policemen with side careers, more corporations selling surveillance software. And worst of all, there will be more of me, walking around in my borrowed suit, full of false business cards and Klonopin. My feet are tingling and it feels like my head is filled with corporate computer code. I have bad energy.

ISIS Videos & Bob
Day 2. At a huge booth that offers “video surveillance and license plate recognition,” two men wearing Buddhist robes are talking with a salesman while a chubby man watches a video presentation. Behind the booth: a huge logo from the Total Recall Corporation, a company named after the 1990 film adaptation of the Philip K. Dick novel. To the left: another booth selling facial recognition software.
On my way back I get ready for more presentations. Back at my booth, I meet Bob from Florida.
“We simulate the identities of enemy combatants,” I say.
I show Bob the video I edited, depicting how we at Syntax Corporation manipulate screen shots from ISIS videos. In one clip, an ISIS fighter from Germany is bathing, fully clothed, in a river with his son. An armed fighter is giving a speech near the river bank. Young boys play in the brown water. At this point the camera moves back to the fighter and the video freezes and zooms in on the face of the man. The face of the ISIS fighter then gets transformed into computer graphics.
“This is brilliant,” says Bob.
I leave my booth to get away from the horror of lying all the time. I decide to take some photos. At a far away section of the fair, I take a photo of a booth that sells infrared bomb detectors and get scolded by an aggressive exhibitor in an oversized grey suit.
“We don’t take photos here,” he says, staring me straight in the eyes. “What are you doing here?”
“I am an exhibitor,” I say. “I am from The Syntax Corporation, we are a Danish company that…”
The man immediately stares at my ID card and then looks me straight in the eye. “This is very unprofessional, Jacob,” he says, reading my name off my ID card.
“Hey relax…” I say, “I am just a fan of your product,” I say, and walk shamefully away.

The New Biometric Locks
I stop at the huge Ametis Corporation stand. They produce advanced biometric locks—access control systems based on the scanning of eyes, faces and thumbs. Derrick, a Canadian man in his late thirties, comes over and explains the system to me.
Derrick shows me a biometric finger scanner and demonstrates how it works. The system also has a face scanner. Derrick points to the two small cameras: stereoscopic vision.
“It’s a security measure,” says Derrick, “In this way we make sure that nobody tricks the system and gains access by placing a photograph in front of the scanner.”
I tell Derrick about Face Jagger, how we at Syntax Corporation are working with biometric simulation, and how we are making 3D printed masks to simulate the identities of terrorists.
Derrick looks at me, suddenly alert.
I tell him that Face Jagger is mainly designed to prevent terrorism—a cyber weapon designed for Psy-Op purposes. I am, in other words, not in the business of “hacking” a system like the one Derrick is selling. But could it work? Could a person wearing a 3D printed face mask from Syntax Corporation get through Derrick’s system? With a discreet pride Derrick explains that no, even wearing a 3D printed mask, you could not gain access.
“You see this?” he says, pointing to the large black shiny surface of the biometric lock. “Behind this surface is an infrared camera. This camera can detect heat. If a person is wearing a mask, we can see it immediately, because the mask will block the heat coming from the human face.”
One hour later, back at my booth, I meet friendly Rebecca from the neighboring booth.
“A lot of people have stopped by your booth,” Rebecca says, and she smiles. “Everybody asks about you.”
FBI Breakfast
It’s early morning and the sun is shining. I walk toward the fair and slip into the Anaheim Marriott Hotel next to the convention center. Inside is a small market where I can buy breakfast. In a hallway, I pass a room with an open door, and it looks like there is a breakfast buffet inside. I realize that this must be the “Former FBI Agents Breakfast” which I had read about in the catalog.
The breakfast is a seated event. The former FBI agents are all seated around large round tables with white tablecloths. There is not a single empty seat left, but perhaps that is good, because I don’t feel like sitting down. Nervously, I keep stacking food on my plate—scrambled eggs, pineapple, mini croissants,—until there is no more space on the plate. Even with my back turned to the speaker, I sense the dumb feeling of paranoid male energy radiating from everybody in the room.

This whole scenario is very different from the movies where competent hi-tech experts and spies discuss how to save the world. This is a circus! When will it stop? Later that day there is a lecture by Cynthia, a private detective from New Jersey. Cynthia talks about The Economic Crime Council, BitCoins, The Dark Web, and Coupon Fraud. Her PowerPoint presentation is full of random clip art (Balloons, cakes, Disney characters etc.) and pictures of ISIS terrorists. Yesterday, I witnessed how Frank, a buffoonish, self appointed “drone expert” from Los Angeles, set off a small drone and tried to shoot it down with a strange gun. The large gun made a loud noise and ejected a net into the air. But the net didn’t catch the drone. Instead, it flew straight towards the face of an LAPD officer, who was forced to duck in order to avoid getting hit by the drone.

Shakespeare
There is a luncheon starting in 45 minutes. At the luncheon, General Frank “Mad Dog” Mattis, who commanded the Marine Corps during some of the most brutal battles of the Iraq War, will give a keynote address. When I arrive, the room is already filled with people seated around round tables with white tablecloths. On the screen, there are colorful computer animations and on the stage, there are lasers and colored lights. The scene is somewhere between a military jamboree and suburban rave.
Most of the seats are taken but I finally find a spot at a table. At my table, two men with a military look about them are deeply engaged in conversation. To my right side are two other exhibitors. One of the guys works for the Finnish police. The other guy, Samuel, is from Tennessee. Samuel is the director of a company called Elsinore Security. I tell Samuel that I am from Elsinore. He tells me that he picked the name Elsinore because of Hamlet and the castle of Kronborg, the real castle where the fictional Hamlet lived. We talk about Shakespeare. Samuel is really into Henry V and he says that everything Henry V was dealing with (betrayal, deceit, war, and so on) is still relevant today.
Then, bizarrely, the song “The Age of Aquarius” (from the hippie musical ‘Hair’) starts to play loudly over the speakers. A large group of uniformed female waiters (all of them Mexican) serve tall glasses of champagne with solemn expressions on their underpaid faces.

The General
General “Mad Dog” Mattis enters the stage dressed in a dark blue business suit. The face of the General is shown on five enormous LED screens so that everybody at the luncheon can see him. His voice is broadcasted through large speakers. He raises his hands to command silence and then he starts. He speaks like a military man would—his voice is loud, booming, and stiff, like he is talking with a small potato in his mouth. He glances over the vast audience.
“I live right in the heart of Silicon Valley and every day you see how technology is going to improve the lives of so many people. At the same time, the double-edged sword of technology is revealing what evil people can do, to the point where a handful of maniacs can endanger the security of billions of innocent people and corporations engaged in honest work.”
The entire Grand Ballroom is silent and respectful, no laughter, no clinking glasses or silverware.
The General now walks to the left side of the stage.
“ISIS is literally bulldozing the borders between Iraq and Syria. It is an attack on the very foundations of what we believe in. Nation states are disappearing. America is right now downsizing its military and we are losing superiority. We thought technology would solve our economy and solve these social problems…”

The General takes a small break and makes some anti-Obama remarks and then he urges the crowd to “vote the right way in 2016”.
After his speech, General Mattis opens up for questions from the floor. There is a question about the American invasion of Iraq. The general pauses for a moment and then he says that we will probably look back at the invasion of Iraq as a mistake.
There is a brief silence and somebody coughs and in the silence after that cough, an awful truth fills the large room. The general finishes his talk and gets a standing ovation.
War Is Black Magic
On my way out, I pass a booth where two younger men in white polos shoot modified Glock handguns on a digitally-projected screen. The guns are real but instead of firing bullets, the guns have been equipped with a laser. The whole setup is a bit like one of those video arcade games where you pay a dollar to shoot ducks or zombies. But in this game, you are not shooting at crude computer graphics—you are shooting at “real” people: actors filmed by high-definition cameras playing out different mass shooting scenarios. Entertainment and war will mix more and more. ISIS knows this and that’s why they have the upper hand. Their filmed executions are entertainment, propaganda, black magic. The American drones seem old fashioned now compared to ISIS’s perfectly orchestrated beheadings, filmed in crisp high-definition video. The evolution of warfare has gone from the domination of land to the domination of sea, domination of air. The next battlefield is cyberspace and ISIS knows this; everybody here at ASIS knows this too. But nobody here really knows what to do about it. The enemy is invisible, their goals are obscure.

Yanniv
Last day at the fair. A few feet away from my booth, I meet Yaniv from Israel. We talk about about propaganda and military deception. Yaniv works for a security consultancy group in Israel. He asks me about Face Jagger and we walk over to my booth and I show him the 3D faces and do my corporate presentation once more, feeling tired and evil, like a junkie thief.
“This is the deal: pre-crime already exists on social networks. FBI and CIA agents operate on Facebook and Twitter to locate terrorists. But there is only so much we can do on social networks,” I say and continue.
“So what you are talking about is incriminating the terrorists and letting ISIS take care of the rest?” Yaniv says and looks at the poster.
“Yes, that is the general idea,” I say.
Yaniv gives me his email address and we agree to stay in contact. I realize that it is probably not a coincidence that it is Yaniv from Israel who has shown the most interest. One premise of Face Jagger is that Western youth will travel to join ISIS in Syria. Although this is already happening, most Europeans and Americans find it absurd that European and American citizens will travel to a foreign country where they have never been in order to betray the countries of their births. But Israel is one of the few places on Earth where terrorists and civilians live amongst each other, in the same cities. The CIA has never managed to infiltrate Al-Qaeda but Mossad has managed to infiltrate Hezbollah. I drink some water, adjust my business cards on the table, and, after a little while, meet Felix, who invites me to show Face Jagger at a security fair in Mexico City.
I check my fake email address and notice lots of emails from fellow exhibitors. I do not understand where they got my email address from, but then I realize it must be from when other exhibitors used their handheld scanners to scan the barcode on my identification card. It is time to get out. As I pack up, I say my goodbyes. Goodbye General “Mad Dog” Mattis, the Country Destroyer. Goodbye to Michael Hayden, King of Spies. Goodbye to the snoops, the snitches, and the hi-tech psychos. Goodbye Worried Facebook Mothers Who Spy on Children. Goodbye to Cynthia, Private Detective from New Jersey. Goodbye to the GS4 Prison Corporation Inc. Goodbye NSA. Goodbye Yellow Security Dragon Mascot. Goodbye Galaxy Control Systems. Goodbye to David The Human Lie Detector. Goodbye Japanese Drone Salesman. Goodbye to Pinkerton Inc. and Siemens and Sony and ASSA ABLOY. Goodbye to the Octopus Corporation and Goodbye to the U.S. Cyber Command. Bye bye.
I leave the exhibition area. Outside, and I look up to the palm trees as they strive for the sun. As I exit the Anaheim Convention Center and head toward Disneyland, I leave my temporary self behind. I walk toward the Little Blue Boy Motel and on my way I pass some of the homeless people of Anaheim. They are are getting ready for the night, camping out in the Disney-themed bus stops. They are wrapped in old blankets and cardboard and their dirty faces are lit up by the white light from their phones.

Postscript
The ghost of simulation is haunting the world.
The new American president and ISIS are both manifestations of this. Both sides are apolitical at heart, both sides have criminal or semi-criminal backgrounds, and both sides were born on the internet. These new figures are much more than monstrous figure heads. Cyber strategies pervades both sides. In other words, the images are more important than the actual events. The virtual is the new real. To attack the image will become more important than to attack the actual person. There are historical precedents for this. Pre-Crime is not new. The counterintelligence directed against American political dissidents in the 1960s and 1970s encouraged internal conflict and the thwarting of planned actions.
Face Jagger is the second installment of a planned “Pre-Crime Triptych.” Each part of the triptych represents an artistic action that deals with the notion of “pre-crime”—a term coined by science fiction writer Philip K. Dick. This concept describes methods of stopping crimes not yet committed. The concept was introduced in a science fiction novel from 1956, but the term could be used to describe many current practices in contemporary law enforcement and military and political strategy. Science fiction not only deals in the art of the possible, but also in the art of the obvious. In that sense, Face Jagger is not a journey into the fantastic, but rather a journey into normality. In each part of the Pre-Crime Triptych, I present an “imaginary weapon” in a real environment. In the past, I have called this artistic practice “sci-fi Conceptual Art” or “Fictionism,” and although those terms were not precise, they helped explain the projects’ operations. A more precise term to describe the technique used in the “Pre-Crime Triptych” would be “The Artefact Method.”
The Artefact Method
1: An artefact, here defined as “a product depicting something from the future,” will be presented in a “real environment” (not an art space).
2: The artist will exhibit and present the artefact in a “real environment.”
3: Nobody in this environment may know that the artist is an artist (this means that the artist must be alone)
4: When the piece is finally exhibited in an art space, it will consist of two elements: the artefact and a documentation of the environment where the artefact was originally exhibited.
“The Artefact Method” is a homemade art form. This art, by default, dissolves walls between literature and art, technology and magic, high art and kitsch. The first part of the Pre-Crime Triptych took place in China and the second part took place in America. The third and final part will take place in Europe. In this way, the triptych will span the three dominant empires today: the Chinese empire, the American empire, and the European empire.
